F5 CVE-2024-41164 (K000138477)
Check if your F5 BIG-IP load balancer device is vulnerable to the MPTCP vulnerability CVE-2024-41164
F5 Security Advisory Reference
https://my.f5.com/manage/s/article/K000138477
Security Advisory Description
When a TCP profile with Multipath TCP enabled (MPTCP) is configured on a virtual server, undisclosed traffic along with conditions beyond the attacker's control can cause the Traffic Management Microkernel (TMM) to terminate. (CVE-2024-41164)
Impact
Traffic is disrupted while the TMM process restarts. This vulnerability allows a remote unauthenticated attacker to cause a denial-of-service (DoS) on the BIG-IP system. There is no control plane exposure; this is a data plane issue only.
Prerequisites
- A virtual / physical F5 BIG-IP device
- SSH / console access to the F5 BIG-IP with administrator privileges to enter the bash shell
Steps
- Log in to the F5 BIG-IP via SSH / Console
- Verify the TMOS software version
show sys version
root@(BIGIP-1)(cfg-sync In Sync)(Active)(/Common)(tmos)# show sys version
Sys::Version
Main Package
Product BIG-IP
Version 17.1.1.3
Build 0.0.5
Edition Point Release 3
Date Thu Mar 21 04:23:27 PDT 2024
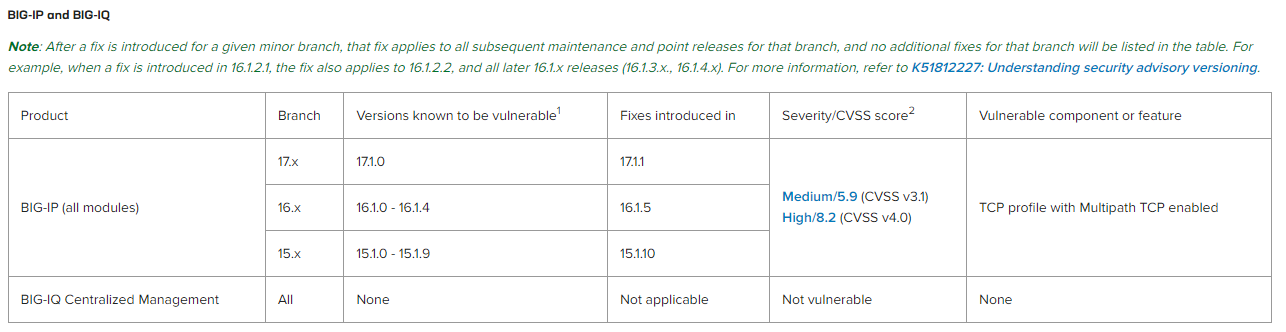
- Check if the TMOS software version matches one of the versions known to be vulnerable as per the table below (click here for the latest tabular information)
- Enter the bash shell
run util bash - Count the number of MPTCP enabled TCP profiles
tmsh -q -c "cd / ; list /ltm profile tcp recursive one-line" | grep "mptcp enabled" | wc -l
* NOTE: This output shows that there is one MPTCP enabled profile configured
[root@BIGIP-1:Active:In Sync] config # tmsh -q -c "cd / ; list /ltm profile tcp recursive one-line" | grep "mptcp enabled" | wc -l
1
- List the names of all MPTCP enabled TCP profiles (if any are configured)
MPTCP=$(tmsh -q -c "cd / ; list /ltm profile tcp recursive one-line" | grep "mptcp enabled" | awk '{print $4}'); echo $MPTCP
* NOTE: This output shows that there is one MPTCP enabled profile configured with the name of "Common/mptcp-mobile-optimized"
[root@BIGIP-1:Active:In Sync] config # MPTCP=$(tmsh -q -c "cd / ; list /ltm profile tcp recursive one-line" | grep "mptcp enabled" | awk '{print $4}'); echo $MPTCP
Common/mptcp-mobile-optimized
- List the names of all MPTCP enabled virtual servers (if any are configured)
tmsh -q -c "cd / ; list /ltm virtual recursive one-line" | grep $MPTCP | awk '{print $3}'
* NOTE: This output shows that there is one virtual server configured named "Common/VS-DELETEME2", which has an MPTCP enabled TCP profile applied
[root@BIGIP-1:Active:In Sync] config # tmsh -q -c "cd / ; list /ltm virtual recursive one-line" | grep $MPTCP | awk '{print $3}'
Common/VS-DELETEME2
- If the results of these checks show that you have at least one virtual server with an MPTCP enabled TCP profile configured then you will need to perform a code upgrade to the corresponding fixed TMOS software version (currently 16.1.5 / 17.1.1)